Setting up SSO
Transcend can be configured to support single sign on with a variety of identity providers to make it easy to manage access control to Transcend. Setting up SSO in Transcend makes it easy to give access to the correct people with the correct scope, all through your existing identity provider.
If you aren't using an identity provider, or would like to manually configure teams and scopes to delegate access to Transcend, see the Access Control Guide.
To get started, go to the Admin Dashboard settings and choose the “SSO” tab. Follow the steps in the next sections to create a SAML configuration.
This section outlines the general steps for setting up SSO in Transcend with an Identity Provider. The following sections provide guides for configuring an application for Transcend SSO for Okta, Google and Azure Active Directory.
You’ll need to create an application in your IDP. We have plans to have official apps in Okta, OneLogin, and other popular identity providers soon. In the meantime, you can create a SAML-based application.
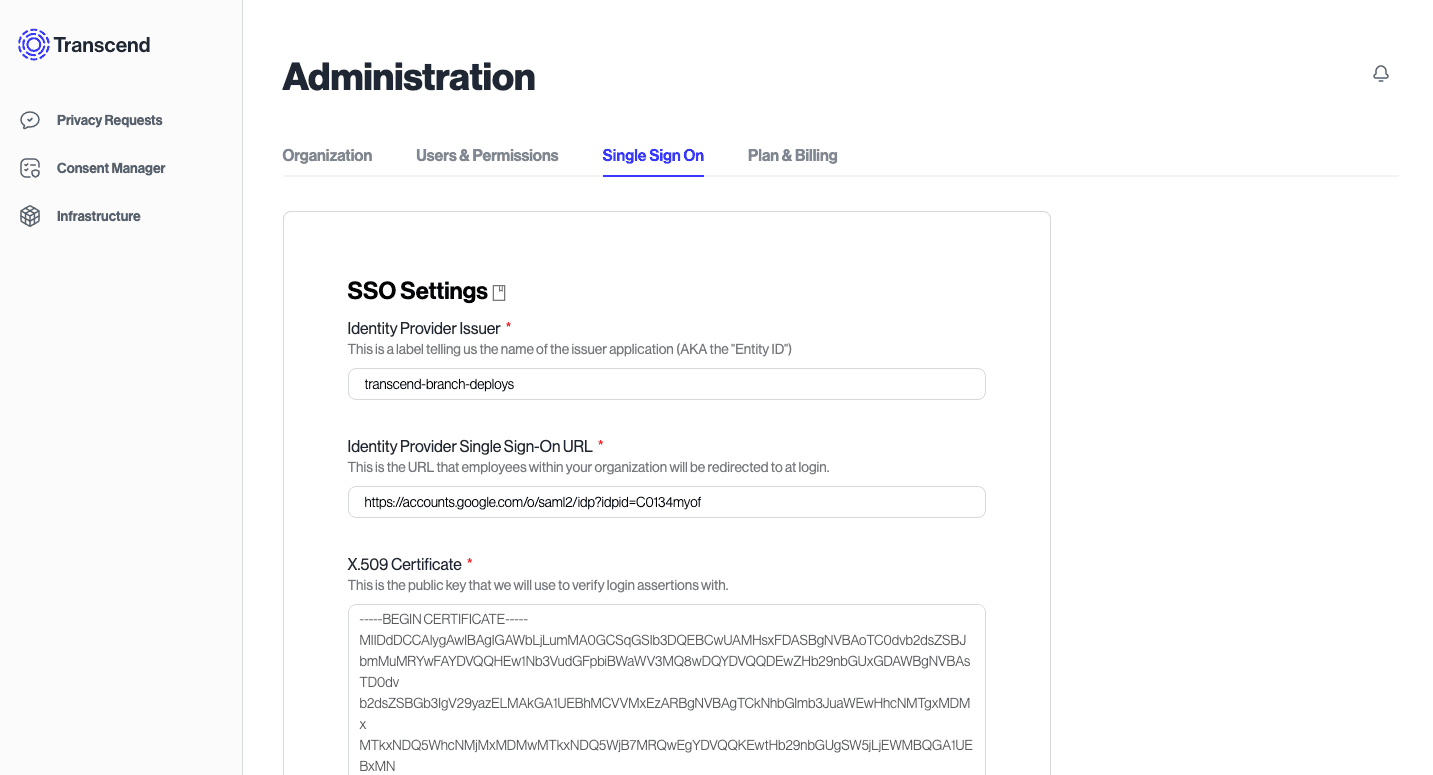
Your provider will ask you for a few things from Transcend, which we provide in the SSO tab.
Once you’ve created the application in your IDP, you can come back to Transcend and proceed.
Your IDP will provide an Identity Provider Single-Sign On URL, Identity Provider Issuer, and X.509 certificate. Copy them into their respective fields in Transcend.
You can now test via IDP-initiated SSO by logging out and logging back in at https://app.transcend.io/login. By entering your email address, you should be redirected to your identity provider.
If you have any trouble along the way, please reach out to us at support@transcend.io.
If you are using our EU-based backend:
- Audience:
transcend - Single sign on URL:
https://api.transcend.io/saml - Recipient URL:
https://api.transcend.io/saml - Destination URL:
https://api.transcend.io/saml
If you are using our US-based backend:
- Audience:
transcend - Single sign on URL:
https://api.us.transcend.io/saml - Recipient URL:
https://api.us.transcend.io/saml - Destination URL:
https://api.us.transcend.io/saml
Review the specific steps for configuring Transcend SSO based on your preferred Identity Provider using the following guides: