Access Control Overview
Transcend allows for granular role-based access control to restrict what your organization members can or cannot do on your organization's Transcend account. Every route that we expose has the ability to be managed from the Users →, Teams →, Scopes →, and Early Access → pages. This means the administrator of your account can dictate which views the users in your Transcend account can see, as well as which changes they can make. We call these access controls scopes.
Throughout our docs, we will indicate when a section is referring to some set of scopes. Look for messages like this to determine how you can configure access control for certain features.
We break down every view we show, and action we allow into scopes. An administrator of your Transcend account can assign these scopes to individual members, or to teams of members within your organization. You can see the set of scopes and which users have access to those scopes on the Scopes → tab under "Administration" settings.
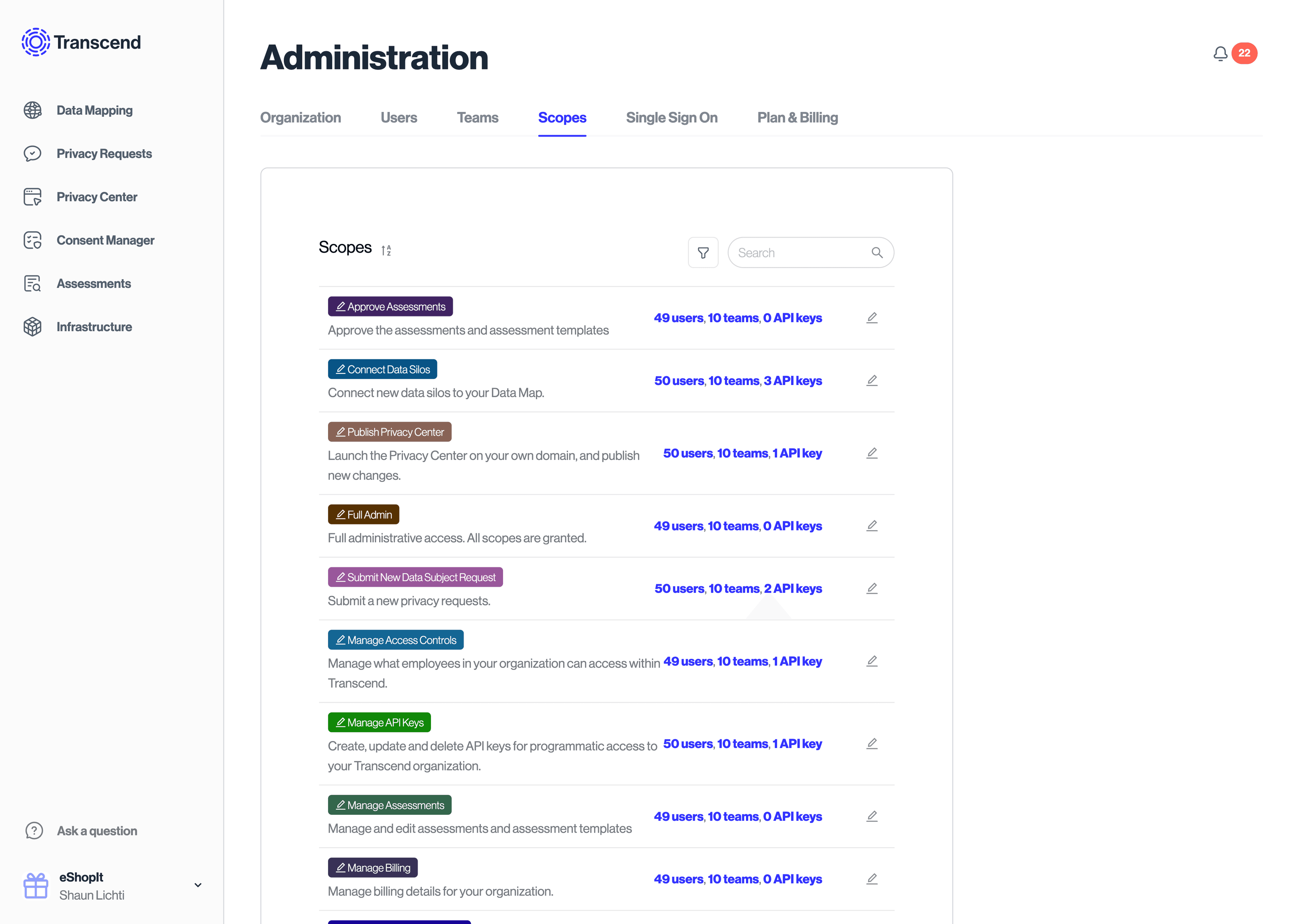
Scopes can also be assigned to API keys. The API keys can be given that same privileges as any member in your organization.
You can manage the assignment of scopes under individual users in the Users → section within Administration. You can manage the assignment of scopes to teams by going to the Teams → section within Administration.
To see a list of all available scopes in the Transcend platform, check out our Scopes & Permissions article.
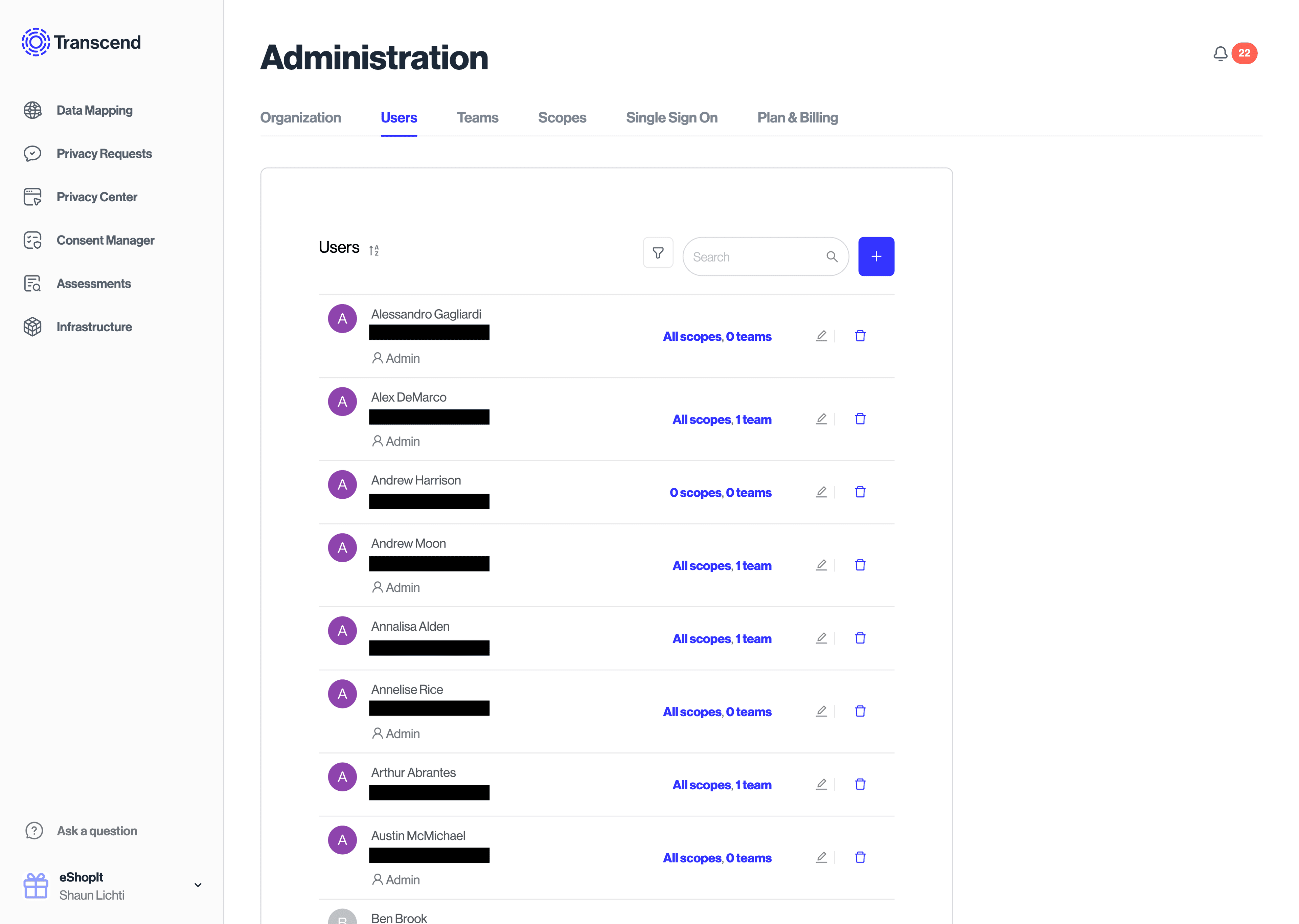
Every employee, partner, or person that should have a log in to your Transcend account is known as a member. By default, each member has no scopes. They cannot see any incoming Requests or private configurations for your organization. The only changes they can make are to their personal account settings.
In order for your members to start doing things like configuring your Privacy Center or Integrations or responding to Data Subject Requests you must assign them scopes.
Learn more about managing user access in our Adding, Revoking, & Auto-Provisioning Access article.
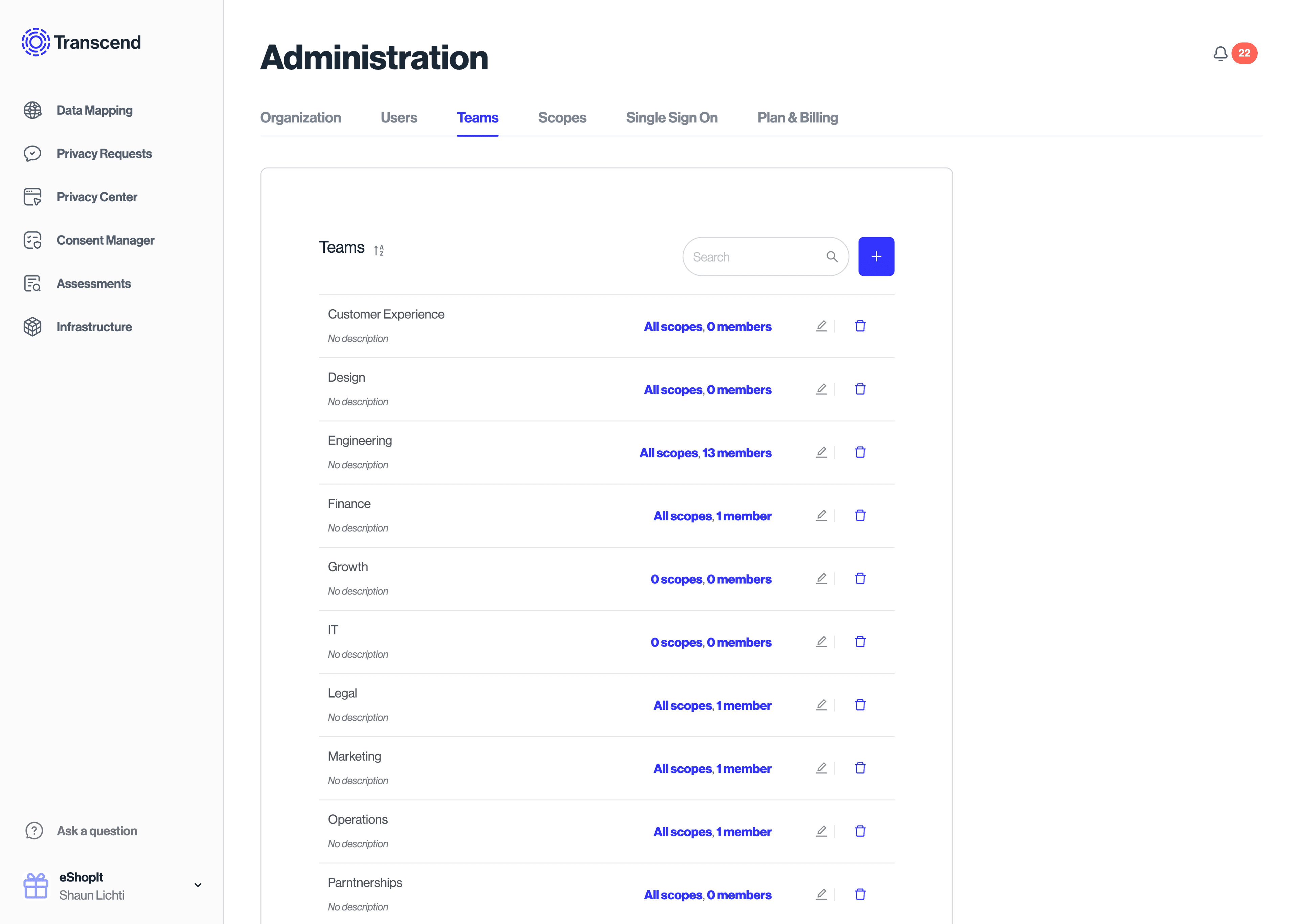
It's common for similar groups of members to be assigned the same set of scopes. For this reason, we allow you to create teams of members, and assign scopes to everyone in that team. If you remove a member from a team, that member will lose the scopes it had from that team unless the member was also individually assigned those scopes. You can create, edit, and modify membership to teams in the "Administration" section under Teams →.
You can manage and invite new "Users" on from your profile icon in the bottom left, then "Administration", then Users → tab, and you can add the user to a specific team when they are invited, or retroactively.
Organization administrators can also manage access to experimental and beta features through the Early Access → tab. This allows your organization to opt-in to new Transcend features before they become generally available.
Learn more about enabling and managing beta features in our Early Access Features article.