Consent Management Capabilities
Key Capabilities of Transcend Consent Management
Transcend Consent Management is powered by airgap.js, our advanced privacy governance SDK. This technology implements a unique set of capabilities that give you unprecedented control over how user data flows from your digital properties.
What it does: airgap.js regulates data at the network level, giving you control over every outgoing request from your website—not just cookies.
Why it matters: Unlike other solutions that focus only on cookie banners and third-party SDKs, Transcend gives you control over all data emissions, including:
- API calls
- Third-party scripts
- Pixel tracking
- Form submissions
- And more
How it works: Through a combination of API monitoring, virtual proxy documents, and optional Content Security Policies, we create a layered security model that controls all network traffic.
With Transcend, you can apply fine-grained controls to each data flow:
| Enforcement Option | What It Does |
|---|---|
| Allow | Permits the data flow to proceed normally |
| Quarantine | Prevents data flow emission until consented |
| Block | Prevents data flow emission and backpropagates optional cancellation signals (irreversible) |
| Override | Modifies the data flow (e.g., removing PII or changing parameters) |
| Omit Cookies | Allows the request but removes cookies |
| Assign Purposes | Tags flows with specific purposes for consent management |
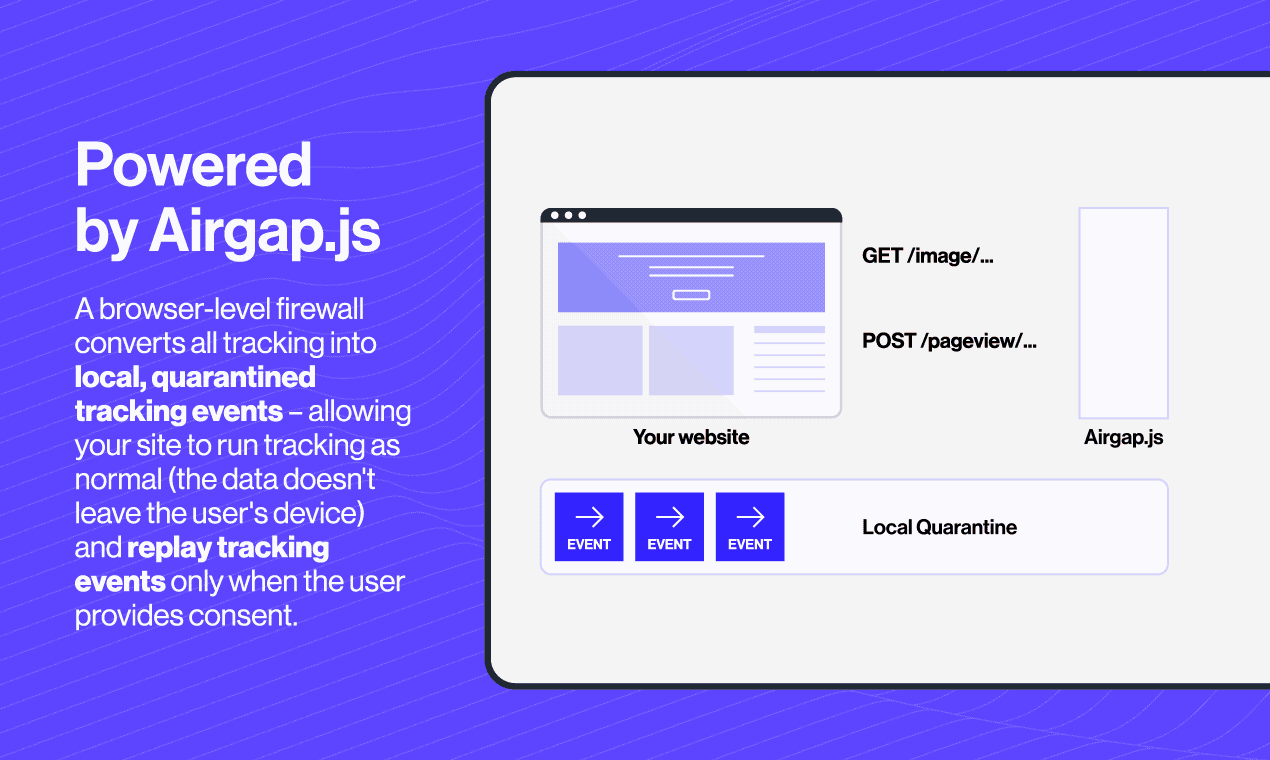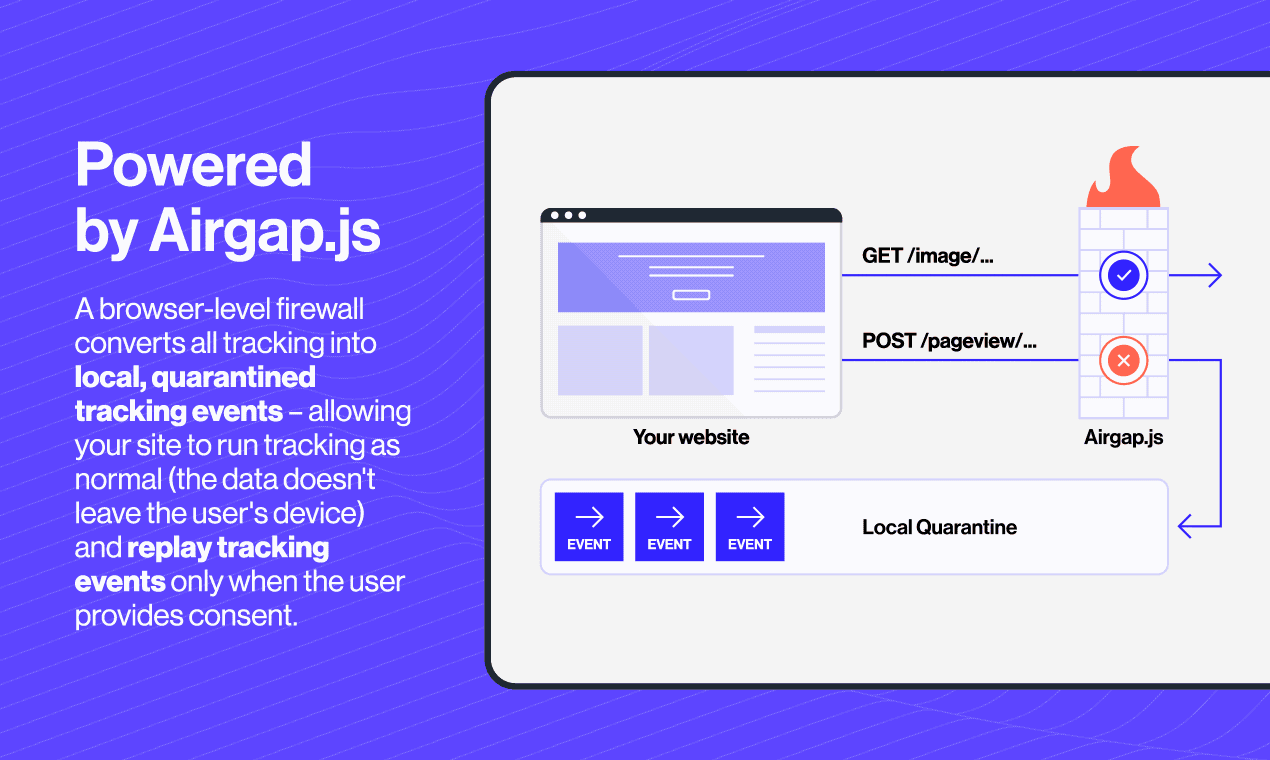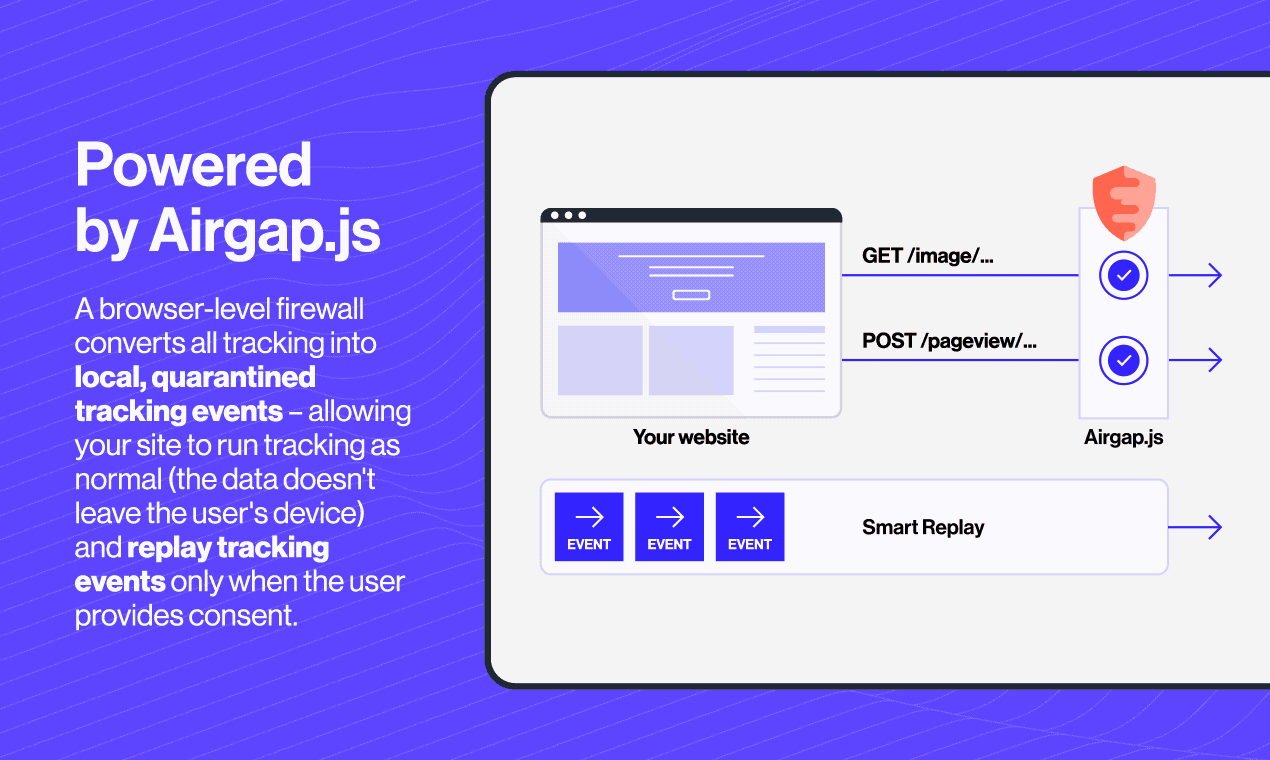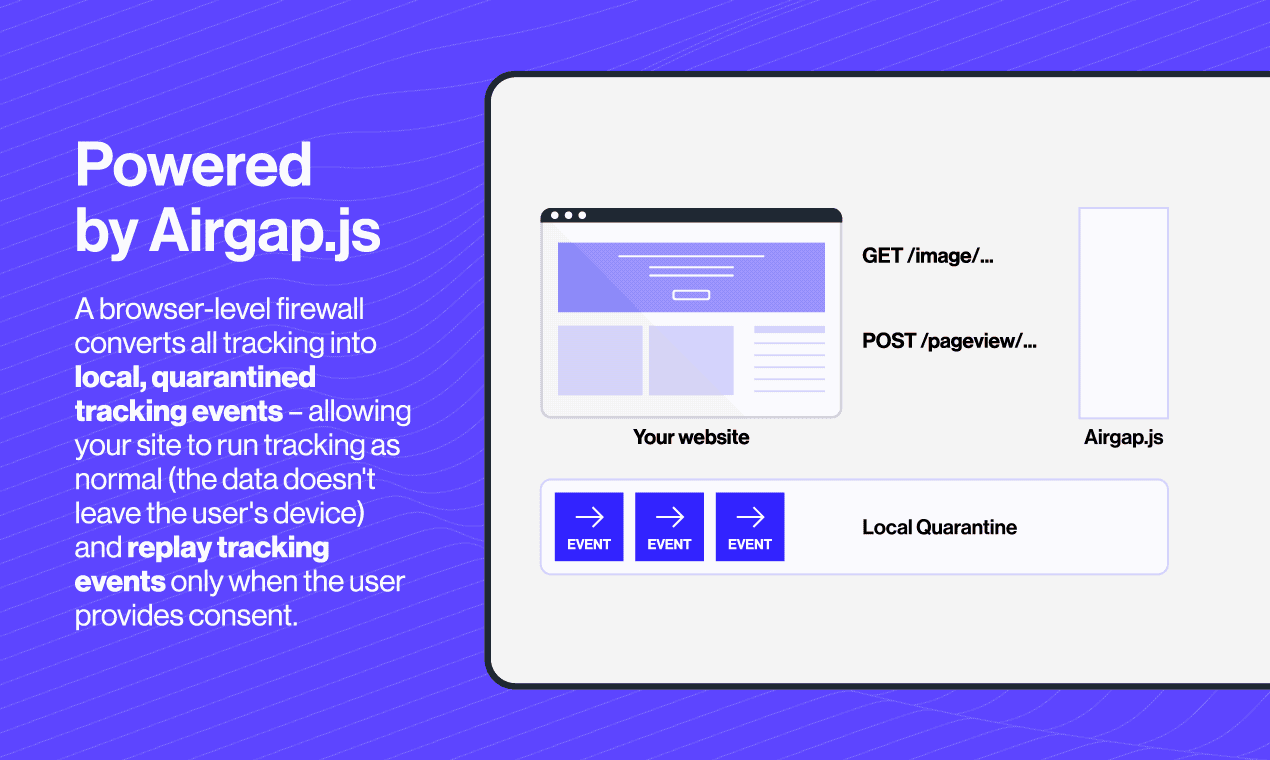
What it does: Our quarantine system temporarily stores blocked network requests and cookies locally until the user provides consent or the events are programmatically approved.
Why it matters: This allows your site to function normally while respecting privacy choices. When a user later provides consent, previously blocked requests can be seamlessly replayed.
Key features:
- Configurable retention: Control how long quarantined events are stored
- Persistence options: Optionally persist quarantine across page views
- Smart filtering: Automatically determine which events are worth quarantining
What it does: When a user provides consent, previously quarantined requests are replayed in their original context.
Why it matters: This enables no-code integration with your website. Your site's JavaScript can operate normally, with blocked requests automatically resuming once consent is granted.
Examples:
- Analytics calls made before consent can be retroactively sent when consent is given
- Tracking pixels that were initially blocked can be loaded later
- Form submissions with marketing consent can be resubmitted when approval is granted
What it does: airgap.js can modify network requests on the fly, allowing you to:
- Force specific query parameters
- Swap domains
- Change paths
- Redact sensitive user data
Why it matters: This gives you incredible flexibility in how you handle privacy compliance, allowing you to implement privacy-enhancing technologies without changing your site's code.
Real-world examples: We use this capability to implement some of our Consent Integrations, which can automatically:
- Enable YouTube's Privacy-Enhanced Mode when applicable tracking purposes are respected and opted out
- Activate Facebook's Limited Data Use mode when applicable tracking purposes are respected and opted out
- Implement Google's Consent Mode for compliant ad tracking
- And much more
What it does: For an added layer of security, airgap.js can generate and enforce dynamic Content Security Policies tailored to users' consent choices.
Why it matters: This provides browser-level protection against unauthorized data transfers, creating a robust defense against data leakage.
How it works: When a user denies consent for specific purposes, the CSP automatically blocks all network requests associated with those purposes at the browser level.
Learn more about Content Security Policies
What it does: airgap.js makes it easy to manage cookies based on consent status by:
- Omitting cookies from specific requests
- Preventing cookie creation without consent
- Removing existing cookies when consent is withdrawn
Why it matters: While controlling data flows can block any data collection event, managing cookies directly adds another layer of protection and helps you meet requirements related to on-device storage, such as the ePrivacy Regulation.
How it works: Our system includes both proactive and reactive cookie protection:
- Cookies can be omitted from outgoing requests
- Cookie creation can be blocked without consent
- Existing cookies can be cleared when consent changes
- Read our blog post: Defeating cookie banners
- Watch our technical deep dive from PEPR 2021:
Ready to get started? Check out our Quickstart Guide or explore advanced configuration options.