DSR Automation Overview
Transcend DSR Automation is a comprehensive and configurable end-to-end process that finds, deletes, returns, or modifies your customers’ data or privacy preferences across your entire tech stack. We support DSR workflows whether you are operating on data that your business owns, or whether you are processing data on behalf of another business.
Transcend DSR Automation fully handles the end-to-end process of a data subject request: receiving the request, authenticating requestors, running preflight checks to confirm the request can be processed, and executing an export or deletion job across all data systems. It also synchronizes user opt-outs across disparate tooling (such as syncing unsubscribes across email marketing systems).
Transcend DSR Automation works with every data system. For unstructured stores, like Slack, Transcend scans for personal data and helps you redact messages in bulk.
With Transcend's catalog of pre-built connectors, you can quickly encode these workflows across your backend and vendor stack. They run with precision and can execute autonomously. Unless you have a manual step in your process, such as an admin approval, you can expect Transcend to execute your requests in minutes.
The detailed list of data subject request types supported by Transcend can be found here.
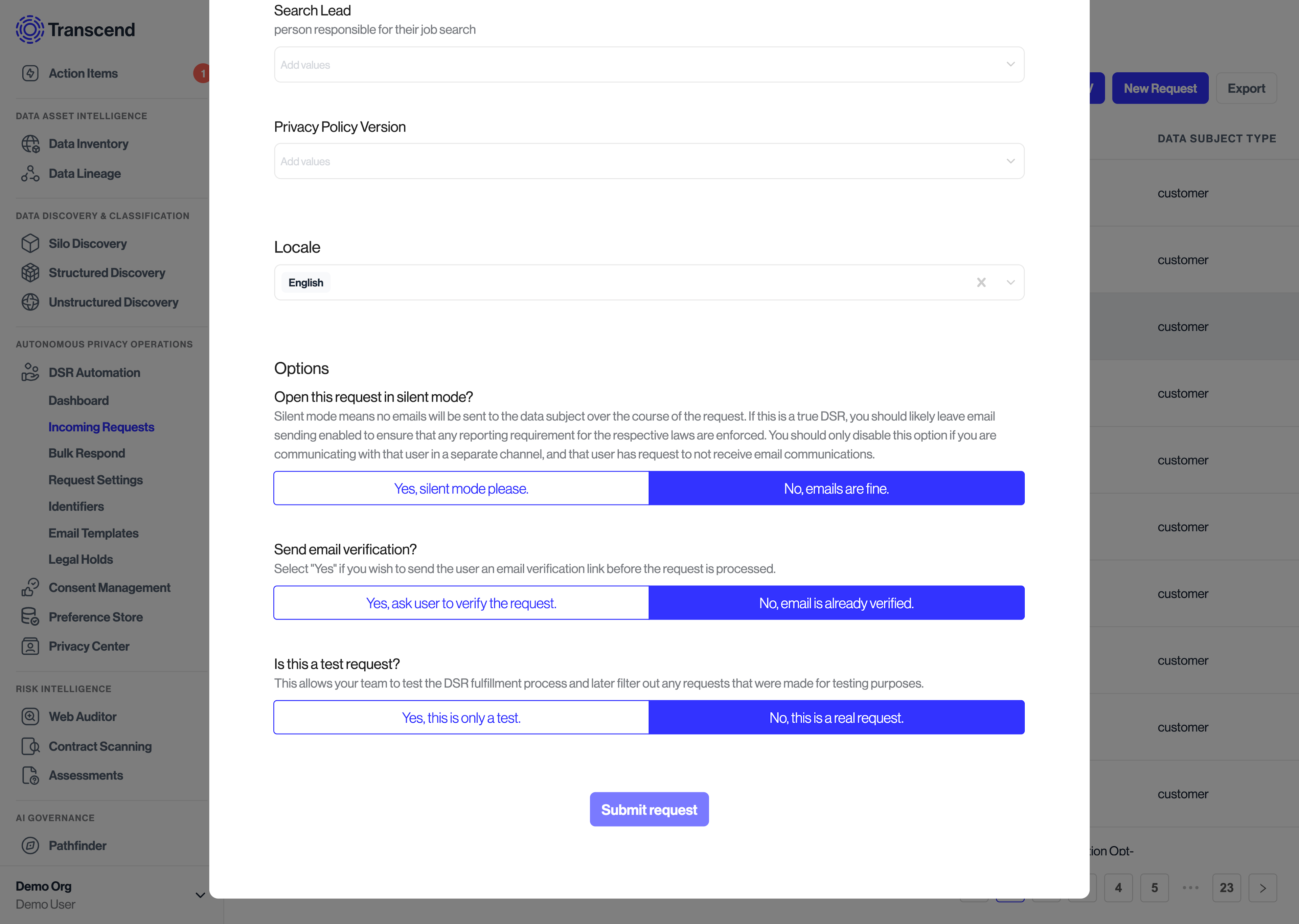
Handling data subject requests at an organization involves several steps, such as authentication of the data subject, processing the request against your systems, and keeping record of the request to ensure it is continuously respected. Every workflow that you set up in Transcend will contain the following modules:
- DSR Ingestion: Requests can be received directly by data subjects via the Privacy Center, indirectly by your existing systems via API, or manually into Transcend via the Admin Dashboard.
- Preflight Jobs and Identity Enrichment: After ingestion, there are several checks that can be performed on the request, such as specific authentication methods, legal holds, waiting periods, or enriching the identifiers provided with any additional identifiers that match the data subject internally (email, phone, advertising_id, user_id, etc.)
- DSR Jobs: Encode the system-by-system rules to be executed for that DSR. For deletion jobs, you can encode the ordering in which those jobs run in the situation where one system syncs data to another system, and for Access requests, you can configure integrations to enable redactions on Access reports.
- Report Delivery: Upon completion of the request, a report of the request is generated and in the case of access reports, can be sent to the requestor.
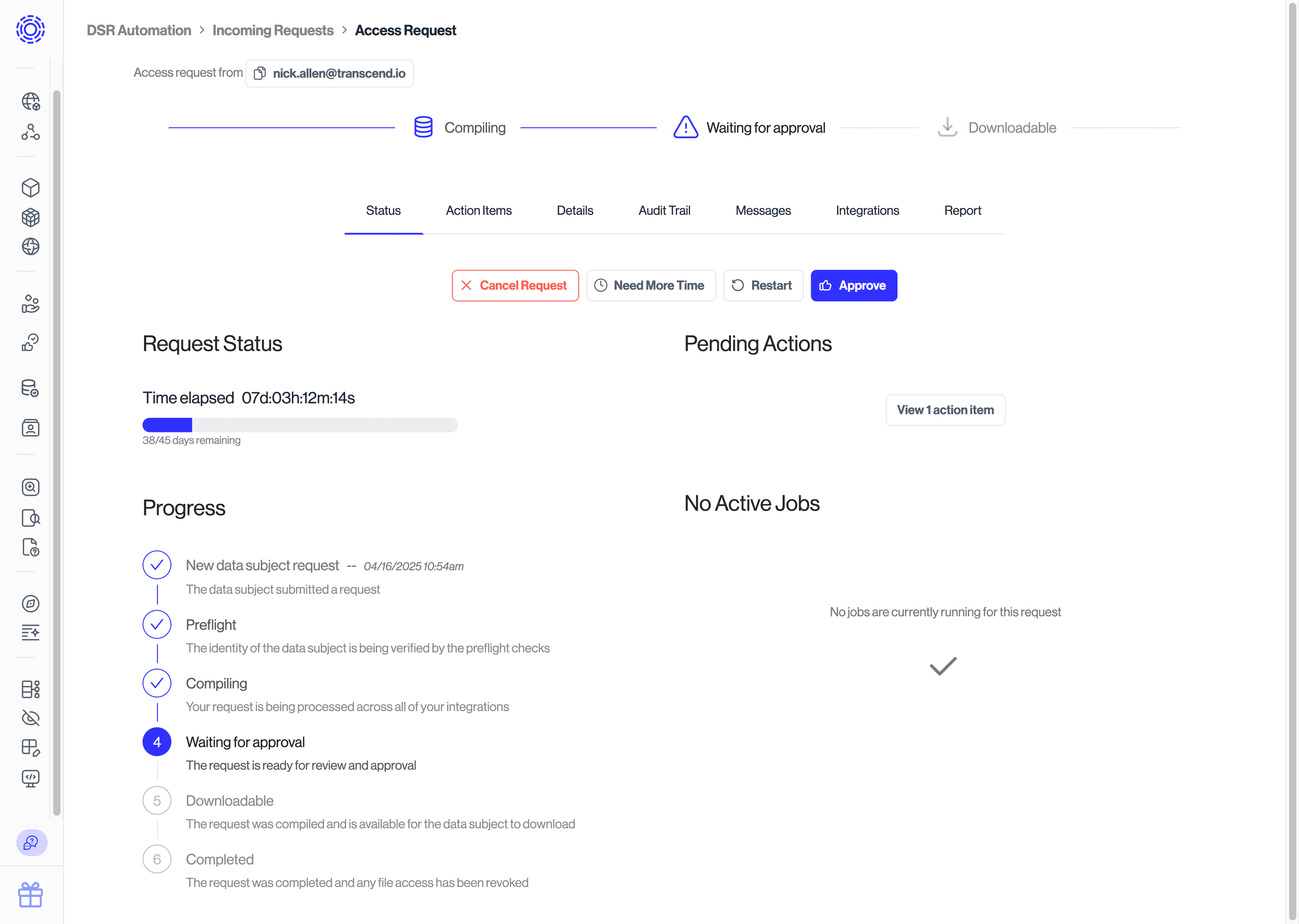
To see the state of a request in this lifecycle, you can click on a specific DSR from the "Incoming Requests" tab of the Admin Dashboard.
Transcend can receive DSRs from a variety of methods including:
- Transcend's DSR API
- Self Service Privacy Center
- Manually submit a Data Subject Request through the Admin Dashboard
- Upload a CSV of Data Subject Requests through the Admin Dashboard
- Forward from your support tool e.g. Zendesk
We offer several methods of ingesting data subject requests, whether you are processing DSRs as a data processor, or a data controller. For more detail, refer to our Data Processor vs Data Controller article.
Before processing begins for a DSR, the DSR is validated by a series of preflight jobs to ensure that it is legitimate and ready for processing. During this step Transcend runs a set of customizable checks. For more information, review the Preflight Checks & Identity Enrichment section of our documentation.
In order to fully process the DSR, Transcend first matches the user’s data in all the different relevant systems (i.e., data systems). During this data processing step, our integrations submit the request on behalf of the user to those different remote systems and make the corresponding API call to act on the data (download, delete, opt out, etc.).
See the full list of DSR statuses here.
Once all jobs have completed and the request has been fulfilled, you can either serve the results via your API, or provide a downloadable report that is also accessible to the data subject via the Privacy Center. The data subject can be notified via email, for which templates can be customized under "DSR Automation" > "Email Settings" > "Email Templates” section of the Admin Dashboard.

Transcend's operations rely on several connections with your internal and external systems. It is important to ensure that each system is communicating properly with Transcend to prevent delays in processing. You can find some troubleshooting steps below, depending on the connection type.
If the issue is with a SaaS connector, you can contact our team for help. We typically patch issues or give recommendations within a few hours.
For internal system connectors, ping the system owner to see if they know why the data system is not reporting properly; you may do so via email through the Transcend platform.
When reconnecting systems, it is also common to switch a request to “Silent Mode” to disable future emails from being sent to the data subject, until Transcend fixes the issues, and the request can properly complete.