AWS Organizations Integration Connection Guide
The AWS Organizations integration enables you to connect multiple AWS accounts at once via System Discovery. The integration is most helpful when you have hundreds of AWS accounts you want to connect with Transcend and don't want to connect one-by-one.
This guide explains in detail how to connect the AWS Organization integration, and how it continuously discovers all the organization's AWS accounts.
There are 4 sets of steps to connect AWS Organization, so that the discovered accounts under the organization can automatically connect. The integration uses CloudFormation StackSet to automatically create the necessary IAM roles in all the organization's accounts.
- Log in to the AWS management account of the organization that you would like to scan.
- Ensure trusted access with AWS Organizations is enabled between StackSets and Organizations. Read this AWS doc for more details.
- Review this guide on connecting downstream AWS services automatically. This is important for setting up the correct IAM policies, database settings, and permissions for automating data discovery of downstream AWS services like S3 buckets, RDS database instances, Redshift clusters, etc.
- Click on Create policy on the AWS IAM Policies page.
- Select JSON in the new tab. Here you can copy and paste the JSON policy that is located in Transcend's connection form under AWS IAM Role.
- As this role will be used in the discovered integrations, if you want to support item-level access for DynamoDB, additional permissions dynamodb:Query can be added for ACCESS requests and dynamodb:DeleteItem can be added for ERASURE requests. dynamodb:Scan can be added for schema discovery and content classification support. Click Next.
- Name your policy (e.g. "TranscendAWSIntegrationPolicy"). Click Create policy.
- Visit the AWS IAM Roles page. Click Create role.
- In Select trusted entity, select AWS account. Here you will put either:
a. For Multi-tenant Sombra™,829095311197(Transcend's Account ID).
b. For Self-hosted Sombra, the account ID of where the self-hosted Sombra is hosted in. - Select Require external ID and copy/paste the External ID provided on our integration connection page. Click Next.

- Search and select the policy you created on steps #1 to #3 (e.g.,). Click Next.
- In Name, review, and create, name the role "TranscendIntegrationRole" and add a description. Click Create Role.
- The name is important because it will be used to automatically connect discovered AWS accounts. While we recommend using the name "TranscendIntegrationRole" as this matches the default name we'll use when later setting up the CloudFormation StackSet, feel free to define a custom name.
Once the role is created, you can navigate to the Trust Relationships tab of the role and the trusted entity should generally look something like this:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::<transcend-or-self-hosted-sombra-account-id>:root"
]
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "5ab4defb0bef8e2bf4b9e636c3949f3edff73c5fb2eb0f56d84a913bd38b8445"
}
}
}
]
}- For self-hosted Sombra, make sure that the Sombra cluster has the permission to also assume the role.
- If you host Sombra via our Terraform Module, you may add this by updating the roles_to_assume variable.
- Otherwise, adjust the IAM permissions attached to the Sombra cluster to have
sts:AssumeRolepermissions on the IAM Role you created.- If your Sombra cluster is hosted on ECS, you would also need to include the role attached to that cluster as well
- The policy should generally look something like this:
{
"Action": ["sts:AssumeRole"],
"Resource": [
"arn:aws:iam::<sombra-account-where-role-lives>:role/<name-of-role>",
"<any other resources ...>"
],
"Effect": "Allow"
}- Visit the AWS CloudFormation StackSets page. Click Create StackSet.
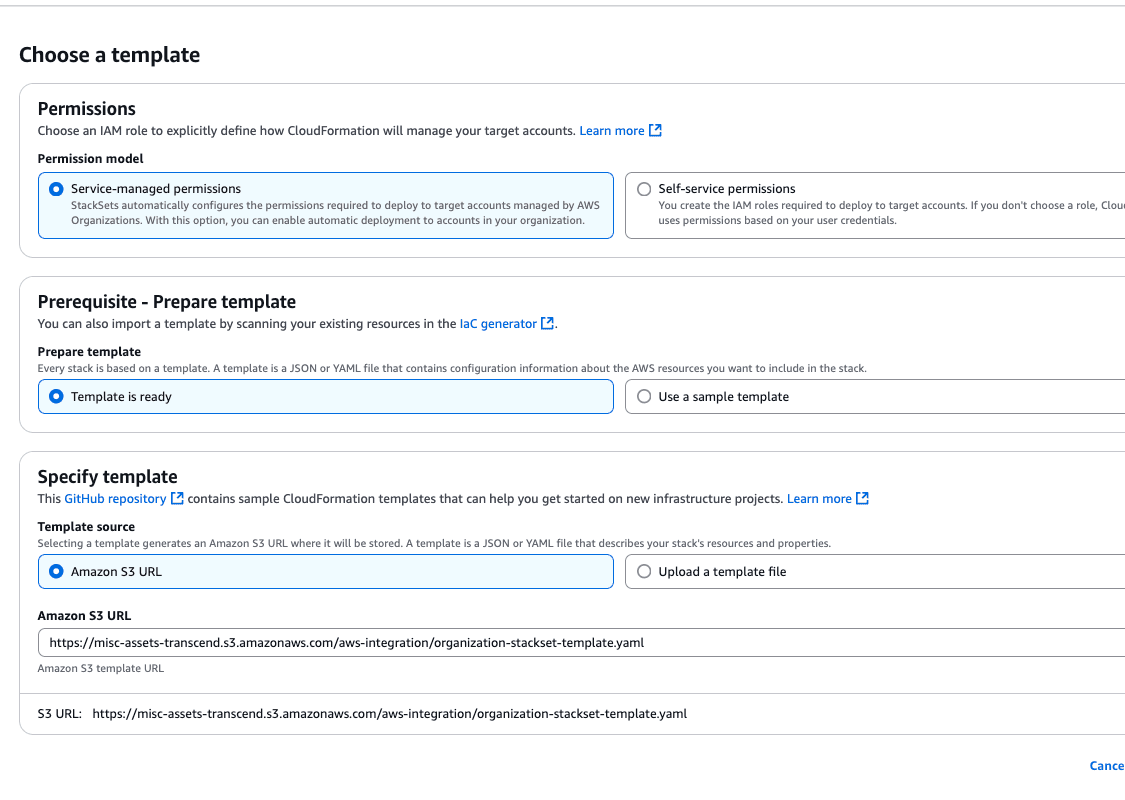
- Choose a template
- For Permissions, keep the default choice of Service-managed permissions.
- For Specify template, copy & paste the template S3 URL here:
https://misc-assets-transcend.s3.amazonaws.com/aws-integration/organization-stackset-template.yaml. This is Transcend's StackSet template file that automatically creates IAM roles in target accounts.
- Specify StackSet details
- In Parameters,
- For ExternalId, copy/paste the External ID provided on our integration connection page.
- For IAMRoleName, this defaults to "TranscendIntegrationRole". If you defined a custom role name earlier, use that instead.
- For TrustedEntityId, put either:
- For Multi-tenant Sombra, 829095311197 (Transcend's Account ID).
- For Self-hosted Sombra, the account ID of where the self-hosted Sombra is hosted in.
- In Parameters,
- Configure StackSet options
- Keep Managed Execution as Inactive so the StackSet performs one operation at a time.
- Set deployment options
- Keep Deploy to organization. This deploys the StackSet across all accounts under the organization.
- Keep Automatic deployment as Activated. This means the StackSet will automatically run for newly added accounts.
- For Specify regions, specify only 1 region. Selecting multiple regions will cause the deployment to fail, as this StackSet creates global IAM resources that are not specific to a region.
- Review
- Click Submit. This will begin the deployment of the StackSet across all the organization's accounts. This can take several minutes depending on the number of accounts. You can view created Stack instances under Stack instances of the StackSet's page.
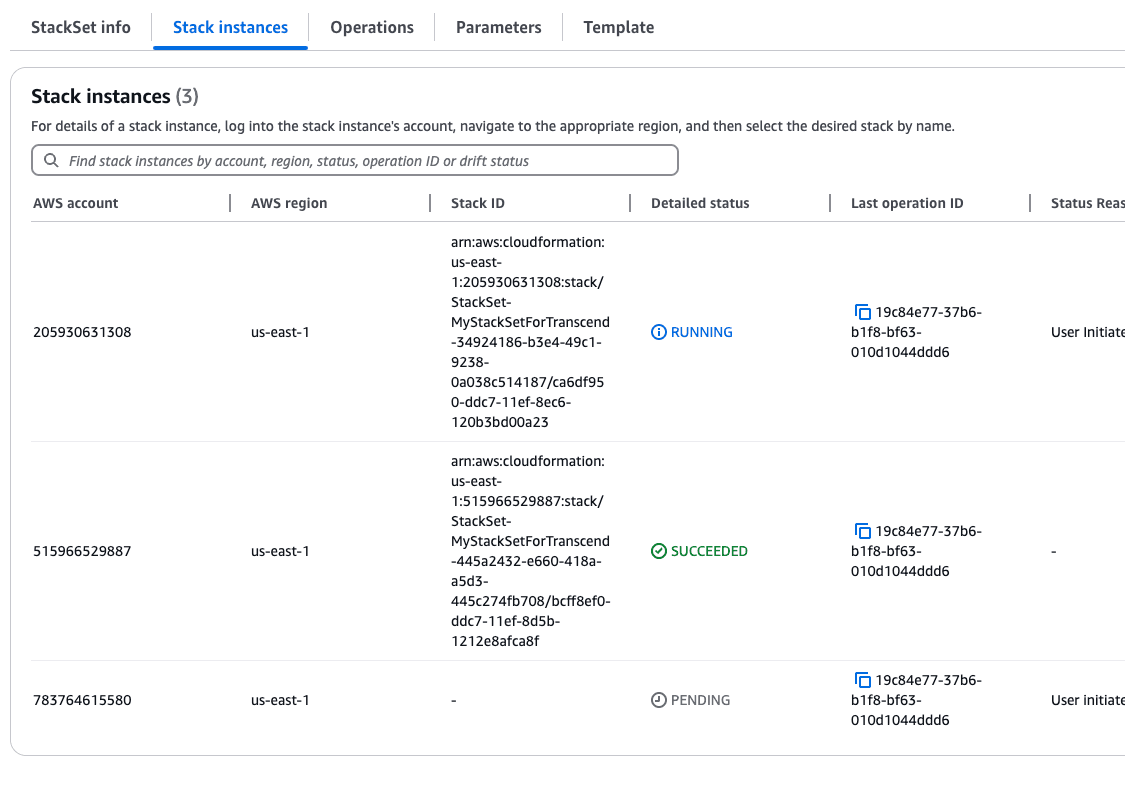
Note: You may notice the management account is not included in the Stack instances. AWS does not create StackSets for management accounts. That is why we manually created the IAM role earlier.
- For the IAM role, enter "TranscendIntegrationRole" or the custom name of your IAM role.
- For the account ID, enter the account ID of your management account. This should be the same account ID associated with the role.
- Select all AWS Regions that you want to run a Data System Discovery scan on. If you want to scan all, then you can leave the field empty.
Finally, connect the integration.
The System Discovery plugin enables automated discovery of all AWS accounts under an organization. The only action you'll need to connect the discovered AWS accounts is to add them to your Data Inventory. You can do this by navigating to the System Discovery page, selecting the discovered AWS account data systems, and then clicking Add to Data Inventory.
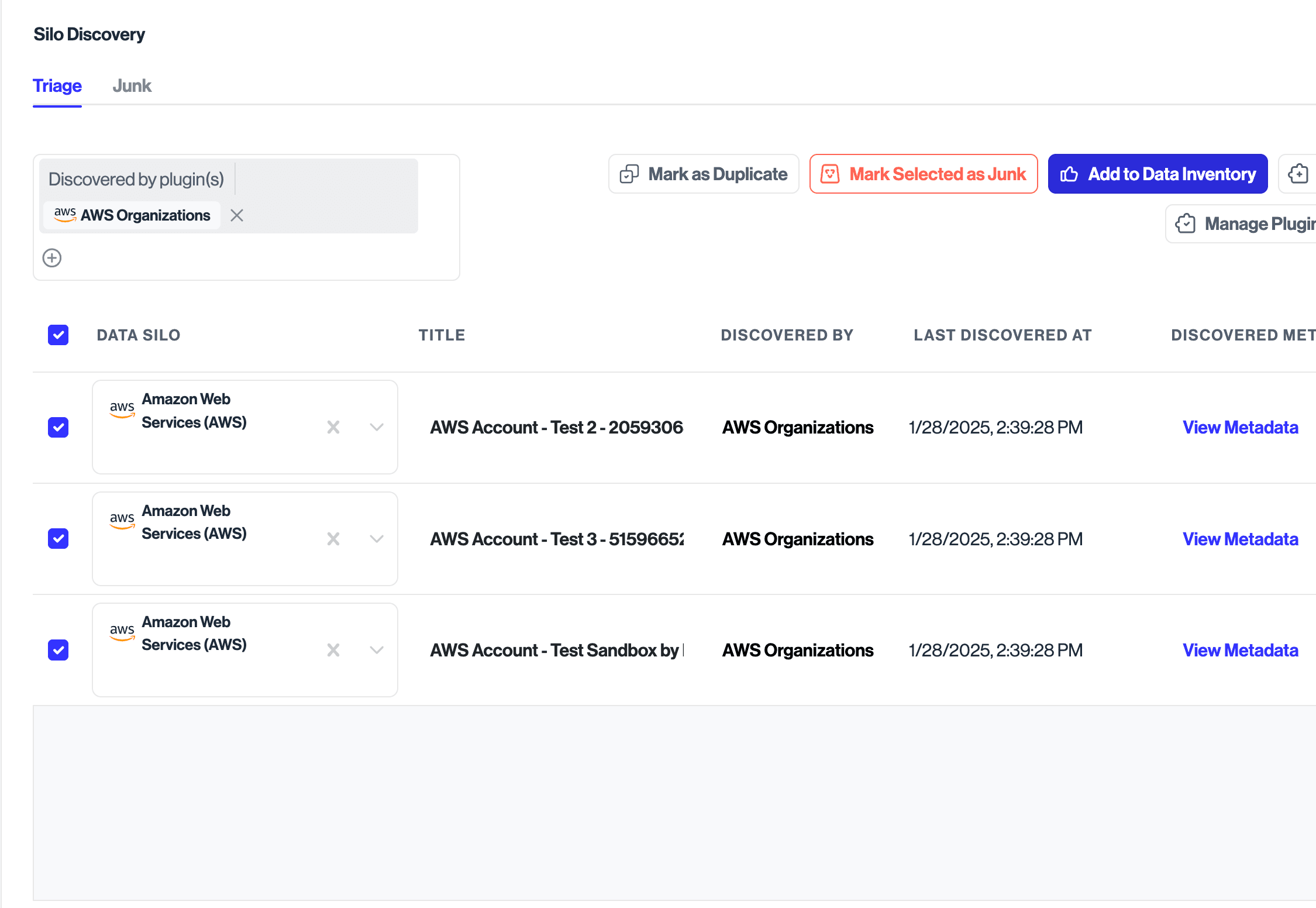
Once added to Data Inventory, you should be able to see your new integrations added under Integrations. These integrations should be automatically connected and its credentials auto-populated.
If you want custom IAM permissions rather than the default ones we provide, you can download and modify Transcend's StackSet template https://misc-assets-transcend.s3.amazonaws.com/aws-integration/organization-stackset-template.yaml. Once modified, in the AWS console, you can edit the StackSet and upload your modified custom StackSet template.
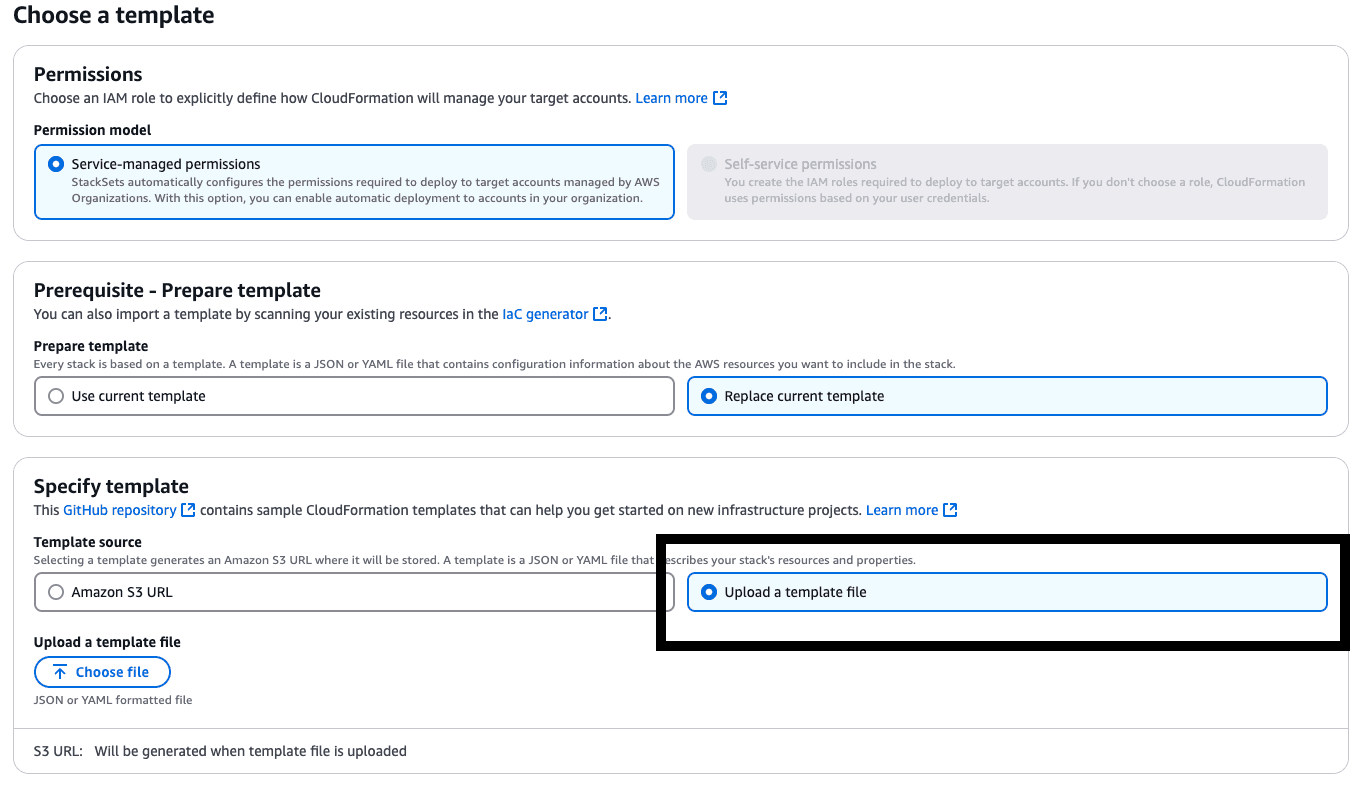
A common reason for this is updating the IAM role's permissions, whether in the StackSet template or the management account's IAM role & policy. To update, simply go through connection steps #2 and #3 on updating the IAM role & policy for your management account and updating the CloudFormation StackSet. All updates should only need to be done in the AWS console, but feel free to re-test the connection in Transcend by clicking Reconnect in the integration page.
We pass the IAM role name from the AWS Organizations connection form input to the discovered AWS account data systems connection input. This enables a fully automated connection process, so you don’t have to manually edit each AWS account integration’s connection info. As long as the same IAM role name with the required IAM policies is used across those AWS accounts, regardless of where the StackSet is set up, auto-connection should work.
An IAM role must exist in the AWS Org management account, as per step #2. This is because StackSets don’t run on the management account itself. This is a known AWS limitation.
You can use the optional "Organizational Units" field in the connection form. Only the accounts under the specified Organizational Units will be discovered during System Discovery.