Transcend's Terraform Provider
Transcend offers a suite of products for privacy management. These products are centered around Transcend’s integration network, consisting of extensive data connections with external SaaS tools, internal databases, warehouses and data systems. Transcend’s official Terraform Provider gives customers options to connect internal data systems to Transcend, organize privacy data and govern their privacy stack in code.
Quickly connect internal data systems to Transcend as they are provisioned.
Use this provider to connect new services to Transcend at the time of initial setup. Incorporating the provider into the provisioning process makes it easy to ensure new data is automatically set up in Transcend for DSRs and classification. For example, if a new database is created, you can use the Terraform provider to add it to your Data Inventory in Transcend, provision a connection string in code and allow for automatic data classification and to enable DSRs.
Discover and classify internal data.
Transcend supports integration plugins with cloud computing platforms, SSO providers and vendor management systems that programmatically scan and discover other systems where data is stored. Common examples of these integrations include AWS, Azure, GCP, Okta and Segment. You can use the Terraform provider to connect and enable the plugins for these types of integrations programmatically using the Terraform provider. See an example of connecting an AWS System Discovery Plugin using Terraform to discover RDS databases, DynamoDB tables and S3 buckets across regions in your AWS account.
Use the Terraform provider to programmatically create new data systems, provision authentication credentials and connect integrations.
Our provider is on the Terraform Registry. Here, you will find complete documentation of our provider and all associated resources and data sources. Once you have an API Key from our Admin Dashboard, you’re ready to get started.
terraform {
required_providers {
transcend = {
source = "transcend-io/transcend"
version = "X.X.X" # fill in with your desired version
}
}
}
provider "transcend" {
key = "<some_api_key"> # Can also be set via the `TRANSCEND_KEY` environment variable
}The most conceptually simple Integration is the Webhook integration, where we send you a webhook with a user’s identifiers and you respond with labeled data about the user. You can setup a server integration with the following code:
resource "transcend_data_silo" "server" {
type = "server"
title = "User Data Webhook"
url = "https://your.company.domain/user/lookup"
description = "Fetches user data from our internal API"
owner_emails = ["david@transcend.io"]
headers {
name = "someHeaderSentWithWebhook"
value = "someSecret"
is_secret = false
}
}Now whenever you receive a DSR, Transcend would send an HTTP request to the https://some.api.link/some/path URL with:
- the custom "someHeaderSentWithWebhook” header seta JWT to validate that the request came from Transcend
- information about the user who submitted the request, and
- the type of request submitted
After a terraform apply, you will be able to see the configured Integration in the Admin Dashboard. As requests come in, you’ll be able to view details about each request, including an audit trail of actions taken relating to user data in this Integration.
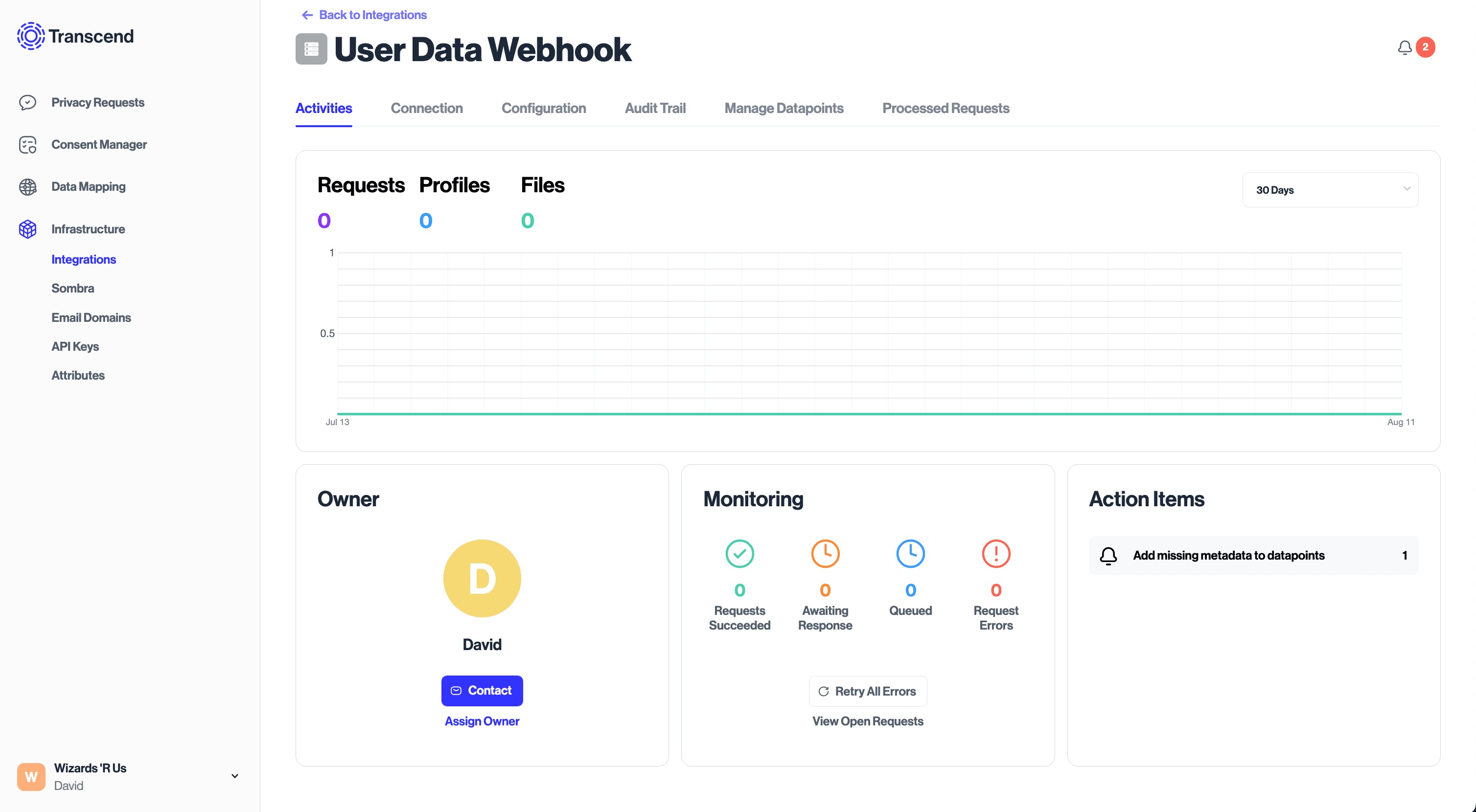
In many cases, connecting an integration with the necessary authentication is all you need to do. As an example, if you are connecting Twilio, a SaaS application that manages text messages and other communications data, our integration catalog will know what data types Twilio has on its users and how to retrieve that data using your credentials.
If you’d like to run an integration’s plugin, you will need to go into the Transcend Admin Dashboard to schedule when the plugin will run, but soon our provider will support scheduling as well.
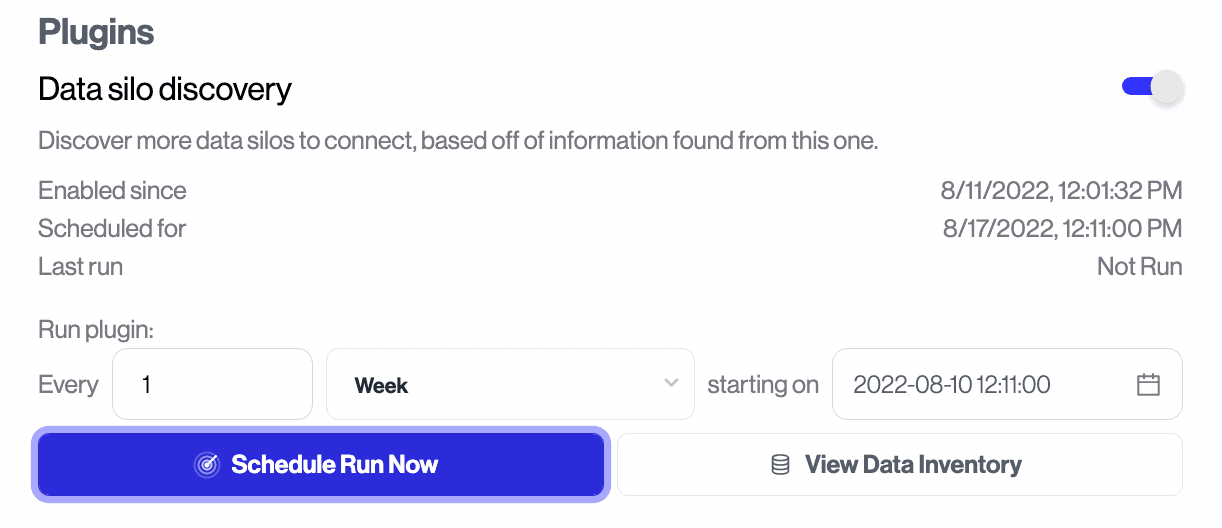
Depending on the scale of how many integrations and datapoints are discovered, it may then be feasible to use Terraform import statements to manage them in code.
Once an integration is connected and a plugin is running, you can label the discovered data and add classifications. In Transcend you can organize the discovered information into subfields - labeling data categories and the purpose of collecting the data using Datapoints. Using Transcend’s Terraform provider, you can do this programmatically as well.
Let’s continue looking at the server webhook integration example from above. When a server webhook is set up, it can return JSON data immediately. Let’s pretend our server endpoint takes in a user ID and returns a user’s email address and location data. We would define a datapoint named User that has properties Email and Location:
terraform-template
resource "transcend_data_point" "server" {
data_silo_id = transcend_data_silo.server.id
name = "User"
title = "User Data"
properties {
name = "Email"
description = "The email address of a customer"
categories {
name = "Email"
category = "CONTACT"
}
purposes {
name = "Other"
purpose = "ESSENTIAL"
}
}
properties {
name = "Location"
description = "The user's estimated location"
categories {
name = "Approximate Geolocation"
category = "LOCATION"
}
purposes {
name = "Other"
purpose = "ADDITIONAL_FUNCTIONALITY"
}
}
}These labels and classifications are used in reports generated and sent to data subjects for DSRs, be used in privacy reports like a RoPA, and generally make it easier to manage your data.
DSRs deal with data across all of your systems, meaning that the final report sent back to a user after an Access request will contain all of the sensitive information your company has access to. At Transcend our highest priority is keeping that data secure and confidential, to the extent that our end-to-end encryption model ensures we cannot see the personal data at all.
This is accomplished by deploying Sombra™, our end-to-end encryption gateway, inside your cloud. When we want to make a request to Twilio to find the text messages you’ve sent to a user, we send the request without an API key to your gateway, which then uses your KMS to add in the API key and sends the request to Twilio.
When you get back the personal data, your KMS encrypts that data before sending it back to Transcend. By using this flow in our integrations, we never have access to your customers’ data in plaintext or in any form we can decrypt.In the context of this Terraform Provider, no personal data is sent through it to Transcend. When we add support in the near future for specifying API keys, those keys will first be sent to your Sombra cluster, encrypted, and then sent to Transcend for storage.