Salesforce Integration Connection Guide
Transcend's Salesforce integration provides Structured Discovery and DSR Automation functionality allowing businesses to:
- Scan Salesforce to surface systems and tools connected to Salesforce
- Identify and classify data stored in Salesforce, including custom data
- Programmatically fulfill DSRs against data stored in Salesforce, with the ability to customize data redactions
Regardless of whether the Salesforce integration will be used for structured data discovery, DSRs or both, the first step is to connect Salesforce to Transcend by authenticating the integration. After the integration is connected, structured data discovery and DSR features can be enabled in the Salesforce data system.
The Salesforce integration is authenticated using the OAuth2 protocol. This allows a Salesforce user to connect the Salesforce integration with the same login credentials used to access Salesforce. The user connecting the integration should be a Salesforce Admin with read and write permissions to ensure the integration functions as expected.
- Navigate to Integrations in the Transcend Admin Dashboard and select or add the Salesforce data system.
- In the Connection section, select
Connectand input the same login credentials used to log in to Salesforce. - A list of scopes used by the integration will be presented. Accept the scopes to finish authenticating the integration connection.
After authenticating the integration, DSR and Data Discovery functionality can be enabled in the data system. The following sections discuss use cases and setup for each.
There are multiple ways that the Salesforce integration can be used within Transcend. For the most expansive usage of the plugin, admin permissions are needed. However, it is possible to create a permission set within Salesforce to scope down the integration's access to only the specific objects that you plan to operate on.
In order to support both Structured Discovery and DSR Automation, the integration will need the ability to both read and write all objects in Salesforce. This allows the integration to discover all custom fields using the Structured Discovery plugins. Then, you can configure DSR Automation to delete or modify any of the objects that are identified as having personal data. The permission set required to do this is close to that of a full admin.
If the user is not using an admin profile, the profile settings of the user will need to have the Customize Application permission enabled. You can find this permission by navigating to the user, and then selecting System Permissions. Within System Permissions, you should be able to find the Customize Application permission.
In order to perform Structured Discovery in Salesforce, but not DSR Automation, it is possible to scope the integration down to simply have read access to the Salesforce objects and fields. With read access, you can index all the fields, pull sample data for each object, and even perform an Access request. Without write access, you will not be able to process data deletion or opt out requests into Salesforce.
In order to create the permission set, you can do the following:
-
As an admin of the Salesforce account, navigate to
Setup > Users > Permission Setsin order to create new Permissions
-
Create a permission set, or update an existing permission set to have the relevant read/write access to the objects that you wish to process by selecting
Object Settingsin the permission set view.-
For each object, select an Object permission:
-
Readaccess is required to perform Structured Discovery and process Data Access Requests for a particular object. -
Deleteaccess is required if you want to hard delete an object as a part of a Data Erasure request. -
Editaccess is required to redact an object as a part of a Data Erasure request, or if you want to persist opt out settings into Salesforce.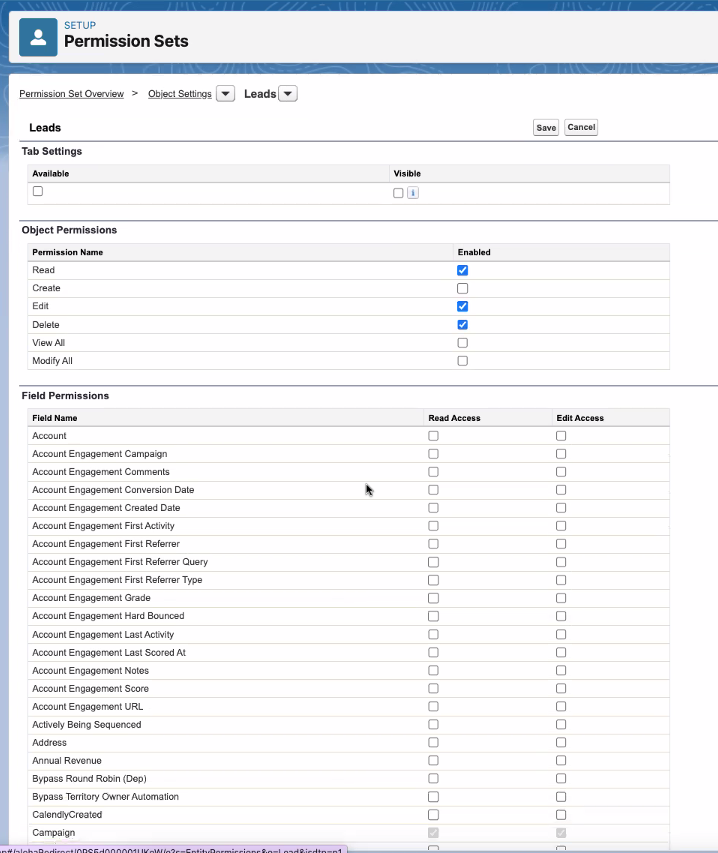
-
If field level access is needed, you can customize which Field Permissions you would like Transcend to have access to. In the case of an Erasure or Opt Out request, you will select fields that you decide to modify. Transcend is capable of modifying any field that you specify.
-
-
In the
Find Settingssearch bar, search forAPI Enabledand enable this for the permission set. There are prerequisites to this on the Salesforce side, such as which edition you have that supports this. You can read more about this here.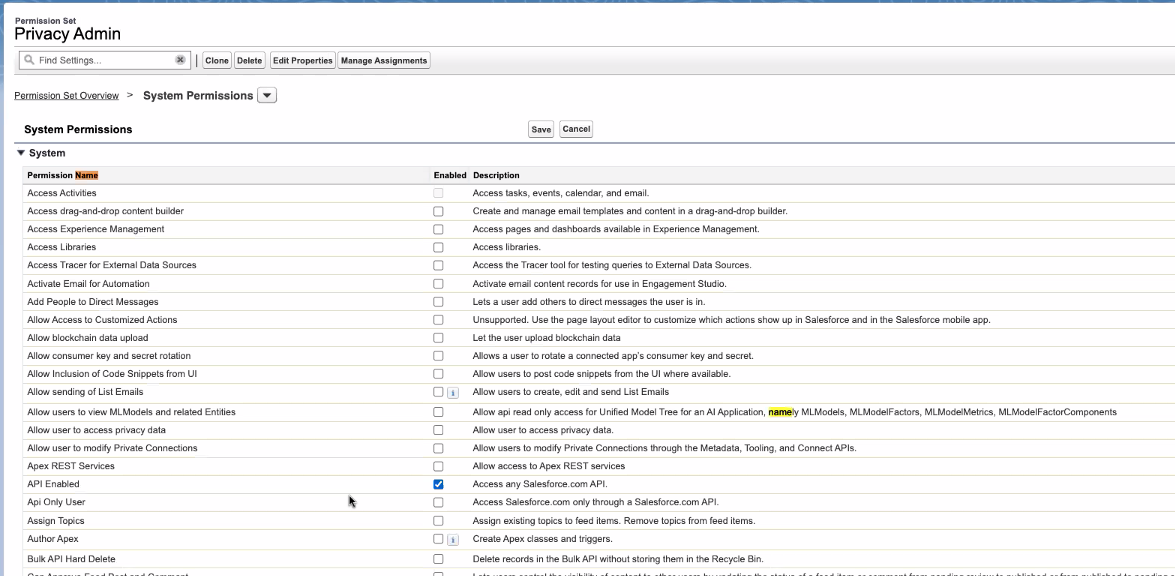
-
Assign the permission set to the user within Salesforce that will be used to connect the Salesforce instance to Transcend. This could be a service account or a real user.
-
Log in to the user or service account with the desired permission set and then authenticate Salesforce to Transcend using OAuth