Understanding Integrations: Discovery
Transcend's Discovery products auto-populate your Data Inventory: a centralized, up-to-date catalog of your company's systems (represented as data silos) and personal data (represented as datapoints and subdatapoints).
A company's Data Inventory view starts with data silos, which can be included in a few ways:
1. Manually added: when a Transcend user adds a silo to a list. Once added, this is an unconnected integration.
2. Automatically connected: Integrations can be automatically connected through a company's Integrations page →.
3. Automatically discovered: Transcend Silo Discovery automatically identifies and recommends silos that a company should add and then connect.
When an integration is connected, relevant datapoints and subdatapoints for that silo will automatically populate into the Data Inventory view →.
Transcend also provides discovery and classification functionality through plugins. There are two types of plugins that can be built into an integration:
1. Silo Discovery:
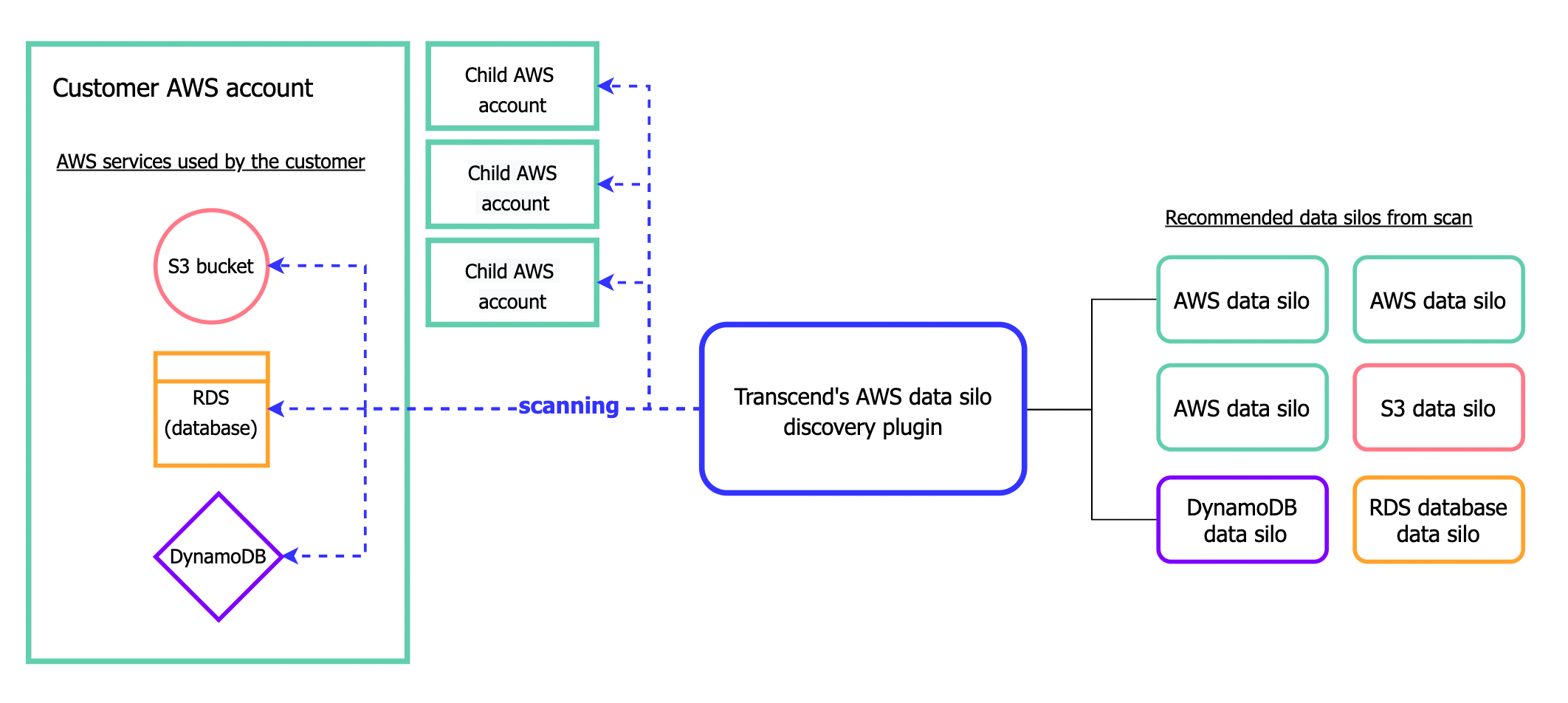
One of the biggest challenges in data visibility and maintaining a unified, up-to-date Data Inventory is identifying which data silos need to be included. This challenge grows exponentially harder as businesses grow—with new tools added, procurement spread across distributed teams, changing system owners, etc.
Silo Discovery enables companies to automatically uncover new data silos and identify which data silos should be added to their Data Inventory. Silo Discovery plugins search a connected integration to identify any additional platforms and systems that share information with the original connected silo. Transcend uses the plugin to find these systems and recommend them as data silos to the customer. The customer can then approve these auto-recommended silos and add them to their Data Inventory, configure them for DSR Automation, etc.
For example, AWS may have datapoints or subdatapoints relevant to personal data rights. However, since AWS has sever services within it, it is a powerful Silo Discovery Plugin:
2. Datapoint Schema Discovery:
Transcend also offers datapoint schema discovery by scanning and classifying unstructured or customizable platforms (e.g., a database). From that scan, Transcend then identifies and suggests the datapoints and subdatapoints likely to hold personal information.
Many SaaS data systems have clearly defined their datapoints and subdatapoints in their API architecture. However, for data systems with customizable architectures or varied implementation (e.g., internal databases, or SaaS with customizable schema, like Salesforce), it is challenging to predefine datapoints and Datapoint Schema Discovery can be particularly valuable in these instances.